Mastering Linux Networking Commands: A Comprehensive Guide
Table of Contents
This article details key Linux networking commands. Earthly ensures developers achieve consistent and reproducible builds on Linux. Learn more about Earthly.
As a Linux user, understanding networking commands allows you to take control of your network environment. Linux offers a robust and versatile networking stack that gives users extensive control and flexibility over their network environments. By mastering Linux networking commands, you gain the ability to configure network interfaces, troubleshoot connectivity issues, analyze network traffic and secure your network.
These commands empower you to optimize performance, ensure reliable connections, and enhance network management.
This article aims to equip you with the knowledge and skills required to utilize Linux networking commands proficiently. By the end of this article, you will have a comprehensive understanding of Linux networking commands and how to leverage them effectively. Whether you are a Linux enthusiast, system administrator, or network engineer.
Basic Networking Concepts
In this section, we will discuss the fundamental networking concepts that form the basis of networking in Linux.
Understanding TCP/IP Protocol Stack
Although the Open Systems Interconnection (OSI) model provides a conceptual and structured way to understand network communication. The TCP/IP protocol stack is the foundation of modern networking and serves as the backbone for communication on the internet.
Imagine you want to message a friend who lives far away. To make sure your message reaches them correctly, the internet defines a set of rules and steps your message must follow. The rules here refer to the TCP/IP protocol.
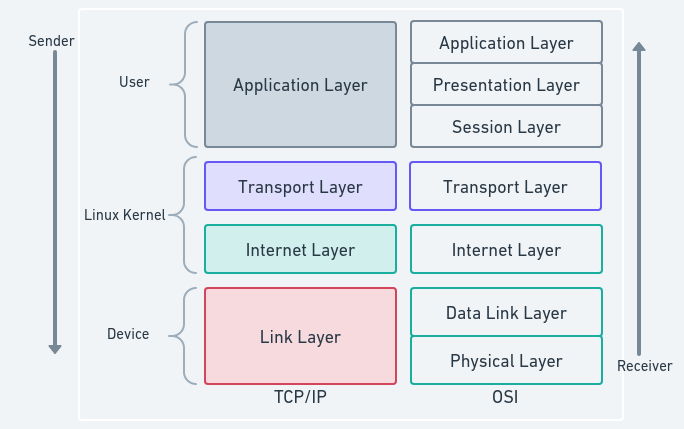
The TCP/IP protocol stack consists of four layers, each serving a specific purpose in the transmission of data across a network. Let’s clarify each layer in the stack:
Application Layer: The topmost layer of the TCP/IP stack, responsible for application-level protocols such as HTTP, FTP, and SMTP.
Transport Layer: Ensures data delivery across the network. The two key protocols at this layer are TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
Internet Layer: Handles data packet addressing, routing, and fragmentation. The Internet Protocol(IP) is implemented at this layer.
Network Interface Layer: Also known as the Link Layer, deals with the physical transmission of data over the network medium. This layer includes Ethernet, Wi-Fi, and Point-to-Point Protocol(PPP).
Understanding the protocol stack lets you comprehend how data is encapsulated, addressed, and transmitted across a network. It also helps you troubleshoot network issues, as it helps identify the layer a problem exists.
To gain more knowledge about network protocols and their workings, take advantage of the various resources available online.
Linux Network Interfaces and Configuration
Network interfaces are the physical or virtual components through which a Linux system communicates with the network. Network interfaces provide a means for devices to send and receive data packets over a network.
Let’s explore the three common types of network interfaces:
Ethernet Interfaces: The most common type of network interface used for wired connections. They have unique MAC addresses and are configured with IP addresses, netmasks, and gateways.
Wireless Interfaces: Used for wireless network connections. They require configuring SSIDs (Service Set Identifiers), encryption keys, and authentication settings.
Virtual Interfaces: Virtual network interfaces, such as VLANs (Virtual Local Area Networks) and virtual tunnels (like VPN connections), allow for segmentation and secure communication over networks.
Linux systems store network configuration details in files like /etc/network/interfaces or /etc/sysconfig/network-scripts/ifcfg-<interface>. These files define IP addresses, netmask, gateway, DNS servers, and more.
Although not covered in detail here you can read up to gain more knowledge of netmasks, gateways, and DNS in the context of Linux systems.
Understanding network interfaces and their configuration is crucial for setting up and managing network connectivity.
Essential Linux Networking Commands
In this section, we will see essential Linux networking commands that allow you to configure, monitor, and troubleshoot network connections.
Packet Internet Groper - ping
ping is a network diagnostic tool used to test the connectivity between two devices on a network. It sends a small packet of data (echo request) to a specified IP address or hostname and measures the time it takes for the packet to reach the destination and return (echo reply).
Syntax:
ping [options] <destination>Common options:
-c(count),-s(packet size),-i(interval), and-t(ttl).Command: ping with interval.
ping -i 2 google.com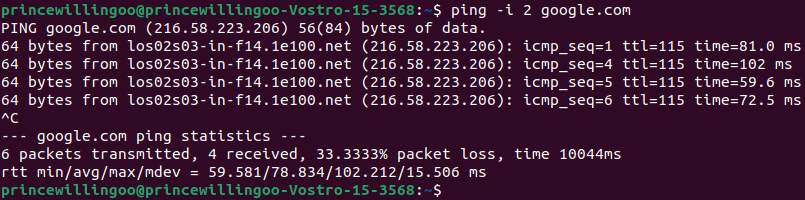
ping command outputThe command continuously sends Internet Control Message Protocol (ICMP) echo requests at intervals (-i 2) to the specified destination (google.com) and displays the round-trip time for each response received from the destination.
Interface Configuration - ifconfig
The ifconfig command enables the configuration of network interfaces. It provides various functionalities such as displaying the current configuration, assigning an IP address, and modifying the parameters of a network interface.
Syntax:
ifconfig <interface> [options]Common options:
up,down,add,del,netmask, and-v(verbose).Command: Configure both IP address and netmask simultaneously.
ifconfig enp2s0 197.210.55.20 netmask 255.255.255.0The command assigns the IP address, 197.210.55.20 to the interface, enp2s0, along with the netmask, 255.255.255.0. This ensures communication within the specified network.
Internet Protocol - ip
The ip command is preferred for configuring network interfaces on modern Linux distributions. It is more powerful and flexible than the ifconfig command and offers more advanced networking functionalities.
Syntax:
ip [ OPTIONS ] OBJECT { COMMAND | help }Useful commands:
ip link,ip address,ip route,ip rule,ip monitorCommand: Remove an IP address from a network interface.
ip address del 192.168.82.100/24 dev enp2s0The ip address del command removes the specified IP address (192.168.82.100/24) from the interface (enp2s0). This disassociates the IP from the interface and prevents it from being used for network communication.
Network Statistics - netstat
netstat is a versatile networking utility that offers comprehensive information on network connections, routing tables, and network statistics. Its functionality facilitates monitoring and troubleshooting of various network-related activities on your system.
Syntax:
netstat [options]Useful options;
-l(listening sockets),-p(program),-t(TCP connections), and-s(statistics).Command: Network traffic in real-time.
netstat -c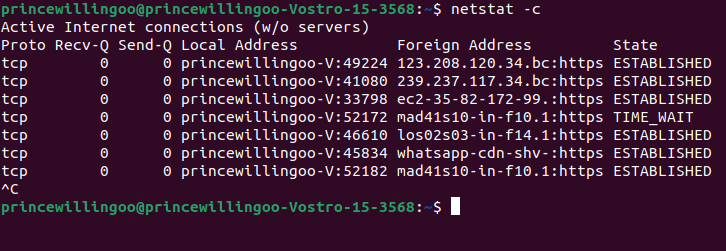
netstat command outputThe command continuously (-c) displays the network connection status, including open ports, active connections, and network traffic information. The output updates dynamically, allowing you to monitor the network activity on your system in real time.
Managing Routing Tables - route
The route command lets you view and manipulate the IP routing table. The IP routing table determines how network traffic is directed and forwarded between different networks or hosts.
Syntax:
route [options] [command] <destination>Common options:
add,del,-net,-v(verbose) and-n(numeric values).Command: Add a route to a network.
route add -net 198.166.0.0/24 gw 10.0.0.1The command configures the routing table to direct network traffic destined for the 198.166.0.0/24 network to the gateway 10.0.0.1. This ensures that network packets intended for the specified network are correctly forwarded through the appropriate gateway.
Tracing the Path to a Destination - traceroute
The traceroute command traces the route packets take from a source to a destination over a network. It provides information about the number of hops (intermediate devices) between the source and destination and the round-trip time (latency) for each hop.
Syntax:
traceroute [options] destinationUseful options:
-n(numeric addresses),-p(destination port),--debug, and-m(maximum_ttl).Command: Traceroute with maximum hops and specific probe count.
traceroute -m 30 -q 3 google.com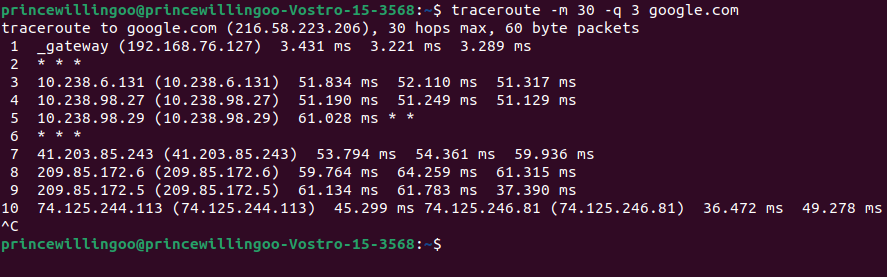
traceroute command outputThe command traces the packet’s path from the source to the destination (google.com) while showing the IP addresses of intermediate devices and their round-trip time. The -m 30 option limits the hops to 30, and -q 3 specifies the number of probes per hop. This helps identify the network path and measure latency between the source and destination.
Domain Information Groper - dig
dig is a powerful DNS (Domain Name System) tool used to perform DNS queries and retrieve DNS-related information. It provides detailed information about DNS records, name servers, and DNS resolution.
Syntax:
dig [options] [domain]Common query options;
+short(short form of information),trace(trace DNS delegation),+recurse(recursive mode)Command: DNS query with trace.
dig +trace google.com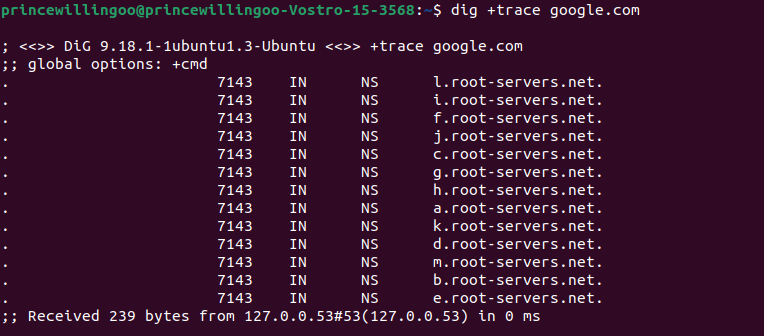
dig command with trace outputThe command traces(+trace) and shows the DNS resolution process from root DNS servers to authoritative DNS servers. The output includes detailed DNS records and IP addresses associated with the domain (google.com). This command aids in troubleshooting DNS issues and understanding the domain’s DNS infrastructure.
Configuring Firewall Rules - iptables
iptables is a firewall utility that allows you to configure and manage the netfilter firewall rules. It provides a flexible framework for filtering and manipulating network traffic, enabling network administrators to set up rules to control incoming and outgoing connections.
Syntax:
iptables [options] [table] <command> [chain] [rulespec]Common options:
--append,--delete,--source,--destination, and--jump.Command: Delete a rule from the firewall.
iptables --delete INPUT -s 192.168.0.10 -j DROPThe command removes the rule that DROPs incoming network traffic from the specified source IP address, 192.168.0.10 in the target chain, INPUT. This enables control over network traffic based on various criteria.
These commands form the foundation for effective network control and troubleshooting in Linux.
Advanced Networking Commands
In this section, we will explore advanced Linux networking commands for network analysis, performance testing, and security assessment.
Socket Statistics - ss
The ss command displays information about active network connections, sockets, and network statistics. It provides a more detailed and comprehensive view of network connections than the traditional netstat command.
Syntax:
ss [options] [filter]Useful options:
-t(TCP sockets),-u(UDP sockets),-n(bandwidth values),-l(listening sockets), and-a(all sockets).Command: Display established TCP connection.
ss -t state established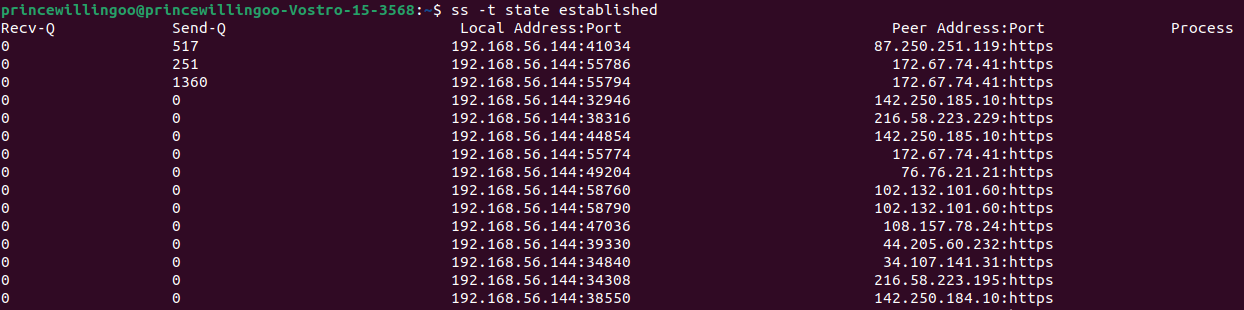
ss command outputThe command displays information about all established TCP (-t) connections, the state of the connection, and other relevant details which are useful for monitoring active connections and troubleshooting networking issues.
My Traceroute - mtr
The mtr command combines ping and traceroute functionality. It provides continuous network monitoring and troubleshooting capabilities. The mtr command sends packets to a specific destination and displays detailed information about the network path, including latency (round-trip time) and packet loss for each hop along the route.
Syntax:
mtr [options] destinationUseful options:
-c(count),-r(report mode),-n(numeric addresses), and-s(packet size).Command:
mtrwith a specific packet count.
mtr -c 10 google.com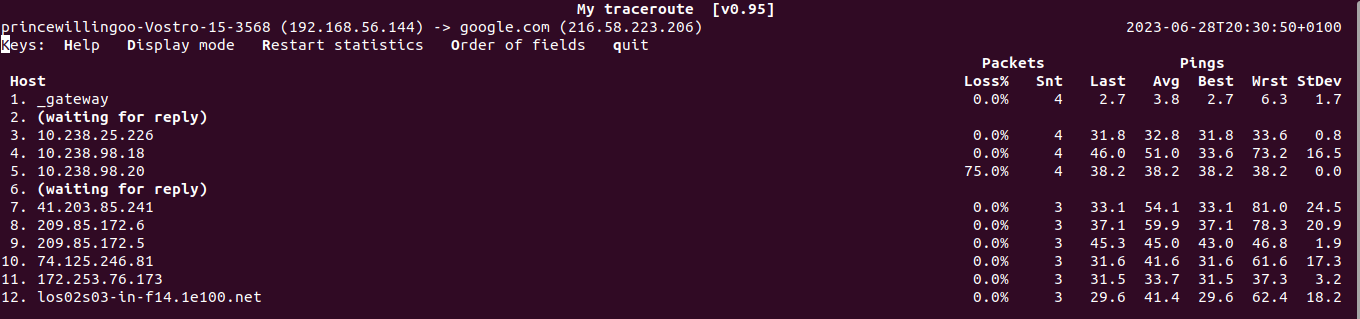
mtr command outputThe command continuously sends packets to the specified destination (google.com) and displays detailed information about each hop along the network path. The option -c sets the number of pings sent. The output helps in understanding the network route.
Analyzing and Capturing Network Traffic - tcpdump
tcpdump is used for monitoring and analyzing network traffic, allowing you to capture packets flowing through a network interface and display detailed information about each packet. tcpdump is commonly used for network troubleshooting, security analysis, and network protocol development.
Syntax:
tcpdump [options] [expressions]Useful options:
-i(interface),-n(numeric address),-c(count), and-s(snapshot length)Command: Capture packets on the wlp1s0 interface.
tcpdump -i wlp1s0 -s 20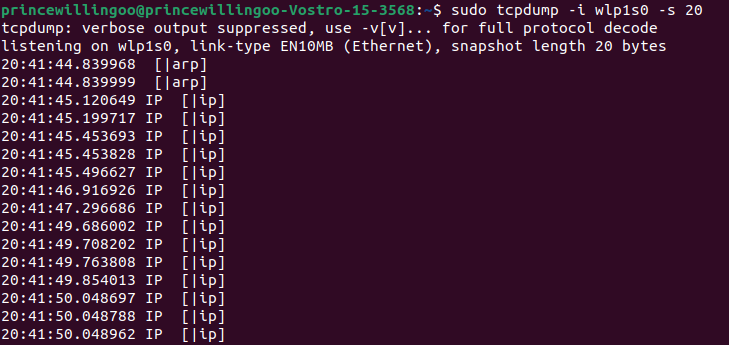
tcpdump command outputThe command captures network packets on the specified interface (-i wlp1s0) and displays detailed information about each packet. The option, -s 20 specifies the snap length. Based on the output you can diagnose network issues, analyze network protocols, and monitor network traffic for security threats.
Monitoring Network Bandwidth Usage - iftop
The iftop command allows you to monitor real-time network bandwidth usage on selected interfaces by displaying a continuously updated list of connections and their corresponding bandwidth usage.
Syntax:
iftop [options]Useful options:
-i(interface),-f(filter code),-n(numeric addresses), and-p(promiscuous mode).Command: Bandwidth usage on the
wlp1s0interface.
iftop -i wlp1s0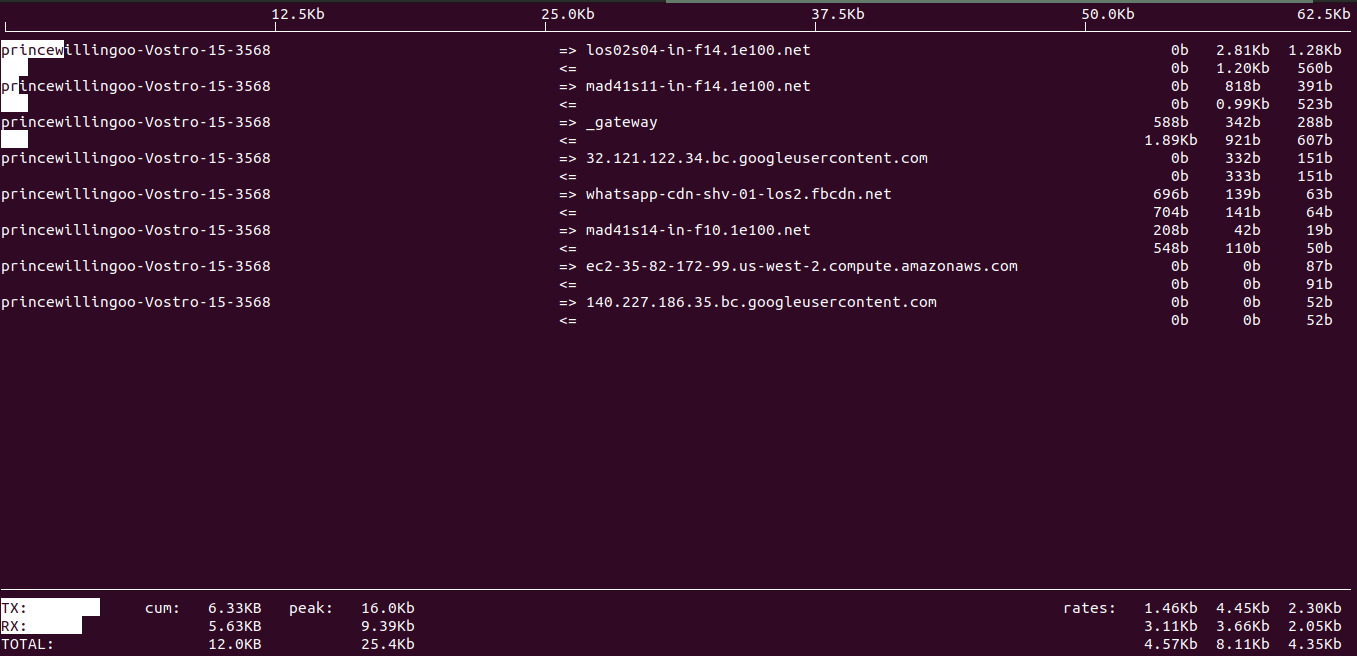
iftop command outputThe command displays a continuously updated list of connections on the specified interface (-i wlp1s0) and their corresponding bandwidth usage. It provides real-time insights into network bandwidth usage, allowing you to identify heavy network traffic or potential bandwidth bottlenecks.
Internet Protocol Performance - iperf
The iperf command is widely used for measuring network performance. It lets you test the network bandwidth between two networked devices by generating TCP or UDP traffic.
Syntax:
iperf [options] [server|client]Useful options:
-s(server mode),-c(client mode),-u(UDP),-P(parallel connections),-t(duration), and-i(interval).Command: Run an
iperfclient with UDP traffic.
iperf -c 192.168.1.100 -uThe command initiates a network performance test between the local machine (iperf client) and the specified server IP address (192.168.1.100) using UDP(-u) traffic. It measures the bandwidth, throughput, packet loss, and latency. The -c implies client mode. The output provides insights into the quality of the network connection between the client and server.
Network Mapper - nmap
nmap is a network scanning tool for network exploration and security auditing. It allows you to discover hosts on a network, identify open ports, gather information about services running on those ports, and even detect security vulnerabilities.
Syntax:
nmap [scan type(s)] [options] [target spec]Useful options:
-sS(TCP SYN scan),-sU(UDP scan),-O(OS detection),-p(port range), and-v(verbose output).Command: Perform a basic TCP SYN scan on a target host.
nmap -sS 216.58.223.206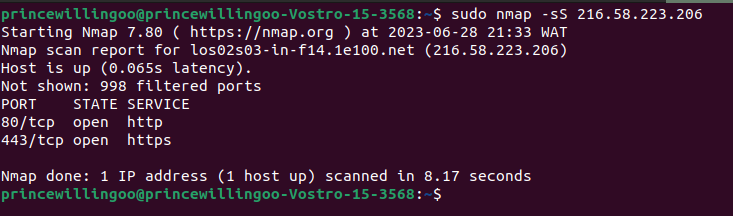
nmap command outputThe command performs TCP SYN scan (-sS) on the specified target host (216.58.223.206) to identify open ports and gather information about the services running on those ports. The output provides a list of discovered open ports, along with their corresponding service information. This can help in network reconnaissance, identifying potential vulnerabilities or misconfiguration in the network, and assessing the security posture of a target host.
By leveraging these commands, you can capture and analyze network traffic, monitor socket statistics, track bandwidth usage, test network performance, and gain deeper insights into network connectivity and performance.
Troubleshooting Network Issues

In this section, we will explore strategies and techniques for troubleshooting common network issues in Linux.
Diagnose Connectivity Problems
When faced with issues or difficulties in establishing and maintaining network connections between systems, try following these steps:
Verify physical connections.
Check the network interface status using the
ifconfigcommand.Test IP connectivity with the
traceroutecommand.Ensure correct IP configuration with the
ipcommand.Use
tcpdumpto capture packets and examine headers for anomalies.
DNS Related Issues
DNS (Domain Name System) related issues are problems or challenges encountered with the DNS infrastructure. To resolve DNS issues follow these steps:
Confirm DNS server settings in
/etc/resolv.conf.Test DNS resolution using
dig.Clear DNS caches if necessary.
Firewall Configurations
Firewall configurations refer to the settings and rules implemented within a firewall to control and manage network traffic. To resolve firewall issues follow these steps:
Verify the status of firewall services (
iptables).Review firewall rules using the
iptables -Lcommand.Test traffic by temporarily disabling the firewall or adding specific rules.
Finally, common networking errors like “Destination Host Unreachable” or “Connection Refused” require checking IP configurations, service availability, and routing tables.
You can effectively diagnose and resolve network issues by following these troubleshooting strategies and utilizing the appropriate commands and tools.
Conclusion
Linux networking commands offer tremendous flexibility and customization options, allowing you to tailor your networking configurations to meet your specific requirements.
Mastering Linux networking commands is essential for working with Linux systems. This article has provided an in-depth exploration of various networking commands, equipping you with the knowledge and confidence to navigate and troubleshoot networking tasks efficiently. Understanding the fundamental concepts and command-line tools discussed in this article allows you to manage networks, diagnose connectivity issues, optimize performance, and secure your systems.
By experimenting with different commands and scenarios, you can expand your knowledge and develop a deeper understanding of the intricacies of Linux networking. With the insights gained from this guide, you are well-equipped to harness the full potential of your Linux systems.
You can continue learning about networking technologies, such as AWS Networking, and Docker Networking.
Earthly Lunar: Monitoring for your SDLC
Achieve Engineering Excellence with universal SDLC monitoring that works with every tech stack, microservice, and CI pipeline.




