How to Create Kubernetes Clusters Locally using Minikube
Table of Contents
This guide provides step-by-step instructions for installing Minikube. Earthly enhances CI/CD with efficient caching mechanisms. Check it out.
Creating kubernetes clusters locally is convenient: you don’t have to mess with production and it’s a low cost way for beginners who are learning Kubernetes to play around. Kubernetes has two tools you can use to create clusters locally which are: Minikube and Kind.
Minikube is a Kubernetes tool used to create clusters locally. This tool is developed by Kubernetes and is free. Unlike Kind which only uses Docker as a driver, Minikube allows you to use Hyper-v or any other virtual machine as the driver.
In this tutorial, you will learn how to install Minikube and create a cluster locally. In addition, you will learn how to secure your cluster using RBAC.
Prerequisites
You need to have installed Kubectl before starting this tutorial.
Installing Minikube on Windows and Creating a Cluster Locally using Minikube
Use the following command to install Minikube on Windows using Powershell:
New-Item -Path 'c:\' -Name 'minikube' -ItemType Directory -Force
>> Invoke-WebRequest -OutFile 'c:\minikube\minikube.exe' -Uri 'https://github.com/kubernetes/minikube/releases/latest/download/minikube-windows-amd64.exe' -UseBasicParsingAfter Minikube has been downloaded, the directory where it is been installed will be displayed:
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/19/2022 12:06 PM minikubeNext, use the following command to add the binary to your path:
$oldPath = [Environment]::GetEnvironmentVariable('Path', [EnvironmentVariableTarget]::Machine)
if ($oldPath.Split(';') -inotcontains 'C:\minikube'){ `
[Environment]::SetEnvironmentVariable('Path', $('{0};C:\minikube' -f $oldPath), [EnvironmentVariableTarget]::Machine) `
}After adding the Minikube binary path, close PowerShell and then open it again using administrator mode whenever using Minikube in the next section.
Use the following command to check if Minikube has been installed successfully:
$ minikube versionIf Minikube has been installed successfully you will get the version number as the output:
minikube version: v1.25.2
commit: 362d5fdc0a3dbee389b3d3f1034e8023e72bd3a7Creating a Cluster Locally using Minikube
Use the following command to start a cluster:
$ minikube start The above cluster will set Hyper-v as the default driver if you are using Windows. However, you can specify your desired driver using the --driver flag and add Docker as your driver:
$ minikube start --driver=dockerWhen Minikube is creating the cluster, it will give you the Minikube version information installed on your computer and the Windows build. This information is critical if your want to use the Windows hyper-v as your driver because not all Windows versions have the hyper-V driver installed or enabled:
* minikube v1.25.2 on Microsoft Windows 10 Pro 10.0.19042 Build 19042
- KUBECONFIG=C:\Users\VET KASI PHONE GSM.kube\configIf you are using an old version of Kubernetes, please go ahead and update it.
* Kubernetes 1.23.3 is now available. If you would like to upgrade, specify: --kubernetes-version=v1.23.3This tutorial uses the hyper-V driver as the driver but you can also use the following tools as your driver:
- Docker
- VMware
* Using the hyperv driver based on existing profileMinikube will go ahead and install all necessary cluster resources needed to start and run the cluster which are: a VM boot image with a version of Kubernetes preloaded.
The process will take roughly 6 minutes but this will vary depending on your internet speed and computing processor.
After the cluster has started successfully you will be prompted with the following message:
* Done! kubectl is now configured to use "minikube" cluster and "default" namespace by defaultUse the following command to check your Kubernetes cluster status:
$ minikube statusYou will the following output:
minikube
type: Control Plane
host: Running
kubelet: Running
apiserver: Running
kubeconfig: ConfiguredUse the following information to get information about pods:
$ kubectl get po -AYou will get the following output:
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system coredns-64897985d-8r2n8 1/1 Running 0 20m
kube-system etcd-minikube 1/1 Running 0 21m
kube-system kube-apiserver-minikube 1/1 Running 0 20m
kube-system kube-proxy-zgzcf 1/1 Running 0 20m
kube-system kube-scheduler-minikube 1/1 Running 0 21m
kube-system storage-provisioner 1/1 Running 1 (19m ago) 20mUsing the Kubernetes Dashboard
The Kubernetes dashboard is used to display your Kubernetes cluster and application’s metrics. This metric is very useful when analyzing the health of your cluster.
Use the following command to display the Kubernetes dashboard:
$ minikube dashboardIt will open the following URL on your default browser:
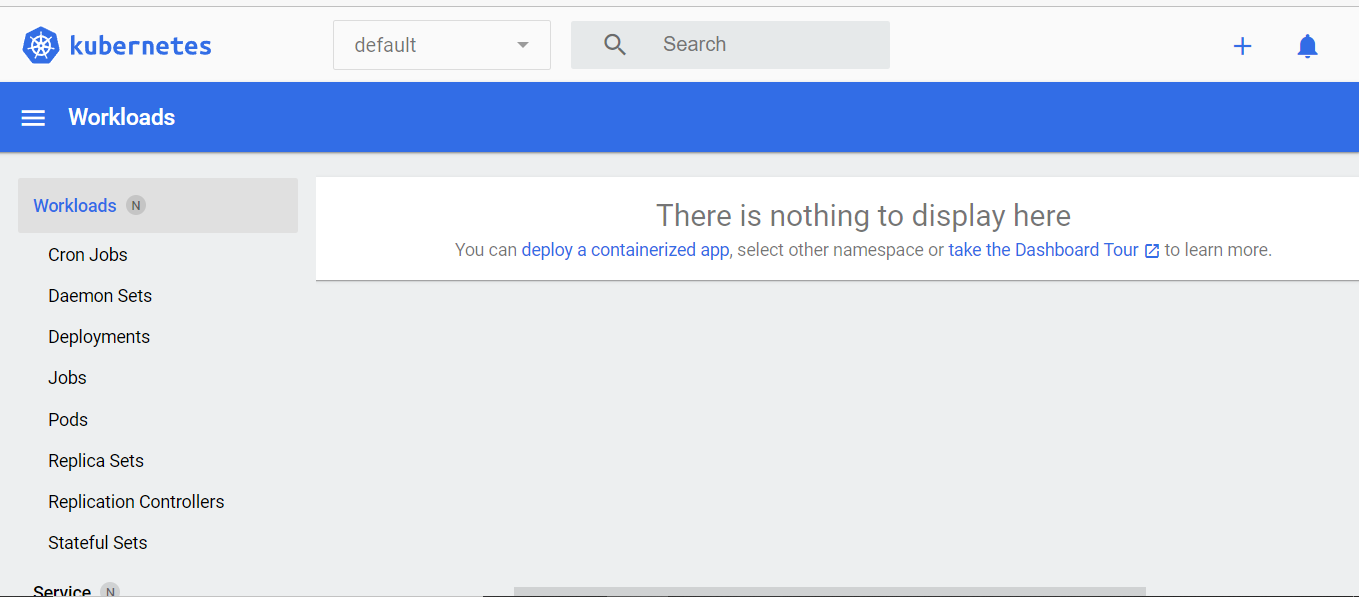
* Opening http://127.0.0.1:3251/api/v1/namespaces/kubernetes-dashboard/services/http:kubernetes-dashboard:/proxy/ in your default browser...Since you have not created any object there will be no details displayed until you created an object:
To get a functional dashboard, go ahead and create a service and deployment using the following command:
$ kubectl create deployment hello-minikube --image=k8s.gcr.io/echoserver:1.4
$ kubectl expose deployment hello-minikube --type=NodePort --port=8080You will get the following output:
deployment.apps/hello-minikube created
service/hello-minikube exposedCheck if the service has been created successfully:
$ kubectl get services hello-minikubeYou will get the following details:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
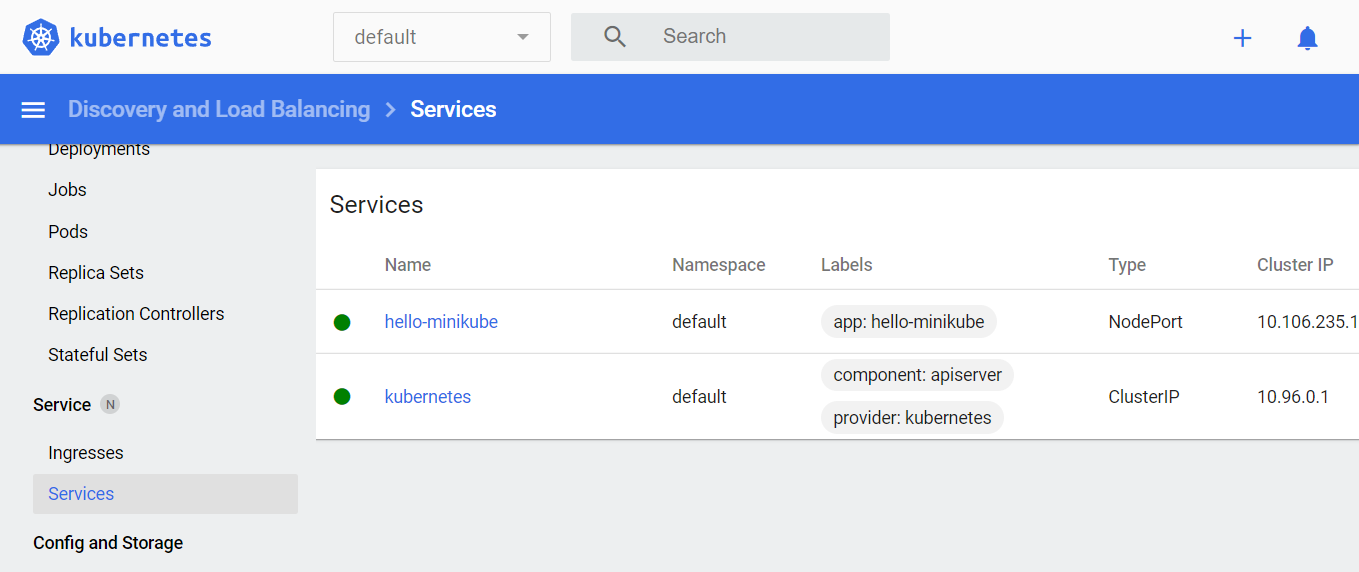
hello-minikube NodePort 10.106.235.150 <none> 8080:30320/TCP 6m53sOnce deployed the Kubernetes dashboard will be filled with the deployment and service created information:
Securing Your Cluster With RBAC
Role-based access control(RBAC) is a Kubernetes technique that allows administrators and cluster owners to set specific access rights for Kubernetes resources in an organization. A ClusterRole is a rule that is set at a cluster scope while a Role applies to a specific namespace.
Creating a ClusterRole
Here is an example of a ClusterRole that gives the user the permission to get, watch, and list the secret resource at a cluster level. The resource field states what resource is being accessed while the verbs field specifies all the actions the user is allowed to take when using the secret resource.
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
namespace: organization
name: secret-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["secrets"]
verbs: ["get", "watch", "list"]Use the following command to create the ClusterRole:
$ kubectl create -f secret-reader.yaml You will get the following output when the ClusterRole has been created successfully:
clusterrole.rbac.authorization.k8s.io/secret-reader createdClusterRoleBinding
A RoleBinding or ClusterRoleBinding connects the Role/ClusterRole with an account or user that is being given the access rights. Verbs are a set of actions that the user is allowed to take when using a Kubernetes resource. For example: get, watch, list.
The following ClusterRoleBinding binds the ClusterRole you just created previously with the default service account. The ClusterRoleBinding also references the previous ClusterRole by stating the name, apiGroup, and the kind of the ClusterRole:
$ kubectl create clusterrolebinding secret-test \
--clusterrole=secret-reader --serviceaccount=foo:defaultYou will get the following output:
clusterrolebinding.rbac.authorization.k8s.io/secret-test createdUsing the following command to display the ClusterRoleBinding file that you have created:
$ kubectl get clusterrolebinding secret-test -o yamlYou will get the following output:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: "2022-04-25T22:39:07Z"
name: secret-test
resourceVersion: "64477"
uid: a0ed20d1-c606-4b03-9364-1f09160243e6
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: secret-reader
subjects:
- kind: ServiceAccount
name: default
namespace: fooCreating a Service
A Kubernetes service exposes your cluster to external traffic. A service enables pod to pod communication. A service has an IP address and a port that is immutable.
You have to specify the service port and target port when creating a port. Create a file called service and add the following contents. This file will create a service called my-service:
apiVersion: v1
kind: Service
metadata:
name: my-service
namespace: default
labels:
app: nginx
spec:
externalTrafficPolicy: Local
ports:
- name: http
port: 80
protocol: TCP
targetPort: 80
selector:
app: nginx
type: NodePortUse the following command to create the service:
$ kubectl create -f service.yamlYou will get the following output:
service/my-service createdYou can get more details about the service you just created using the following command:
$ kubectl get servicesYou will get the following output:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
my-service NodePort 10.103.214.169 <none> 80:30832/TCP 5m46sSetting Cluster Resource Limits
Cloud infrastructure and Kubernetes are expensive; it’s either you’re deploying your cluster on the cloud using Google Kubernetes Engine or creating them locally. Costs will still incur because the cloud is expensive and so does memory. The consequence of not affording Kubernetes is noisy neighbors that hurt cluster performance.
Luckily, there is a mechanism called resource limit that enables you to set pod resource limits. These limits prohibit containers from overspending memory and CPU resources.
The resource limit and request mechanism have three fields which are
ephemeral-storage: This field specifies the ephemeral storage your container can use.memory: This field sets the memory limit threshold or memory request for your container.cpu: This field sets the CPU resource limits or requests for your container.
The following Pod has requests and limits for every container. The first container has a memory limit set to 128 Mi and the CPU resources set to 500m.
apiVersion: v1
kind: Pod
metadata:
name: pod-example
spec:
containers:
- name: app
image: gcr.io/google-samples/gb-frontend:v4
resources:
requests:
memory: "64Mi"
cpu: "250m"
limits:
memory: "128Mi"
cpu: "500m"These changes will be applied when the Pod object is created or applied using the following command:
$ kubectl create -f pod-example.yamlYou will get the following output:
pod/pod-example createdConclusion
By now, you’ve learned how to install Minikube on Windows, set up a cluster, create a service, manage resources and secure it using RBAC. As you continue to explore and enjoy Kubernetes with Minikube, consider taking it up a notch. Optimize your builds with Earthly. It’s a great tool to further enhance your development process. So go on, have fun testing out your Kubernetes clusters locally with Minikube and maybe give Earthly a try!
Earthly Lunar: Monitoring for your SDLC
Achieve Engineering Excellence with universal SDLC monitoring that works with every tech stack, microservice, and CI pipeline.